Guide to Web App Pen Testing
Table of Contents
- What Is a Web App Pen Test?
- What is the Goal of Web Application Penetration Testing?
- Types of Web Application Penetration Tests
- Web Application Penetration Testing Methodology
- Web Application Penetration Testing Tools
- Custom Developed Web App Pen Testing Tools
- Penetration Testing Certifications
- Automated vs.Manual Web App Pen Testing
- Contact Us
What is a Web App Pen Test?
Web application penetration testing, often referred to as a “web app pen test,” “application pen test,” or “website pentest,” is a simulated cyber-attack against a website to identify exploitable vulnerabilities. This security assessment involves testing a website, APIs, login features, e-commerce platforms, and online services to uncover weaknesses that hackers could exploit.
A web application penetration test involves systematically examining various web application components, including application protocol interfaces (APIs), frontend and backend servers, login protocols, and code development practices. The primary goal is to uncover vulnerabilities, such as inputs susceptible to code injection attacks and other common threats.
During a web app pen test, the expertise of security professionals and ethical hackers is crucial. They use the tactics and techniques hackers employ to access and exploit security flaws. A web application pen test is a proactive test that identifies vulnerabilities before they can be used in a real-world attack. By performing these tests, organizations can test and improve their security controls, protect sensitive data, and ensure the integrity and availability of their web applications.
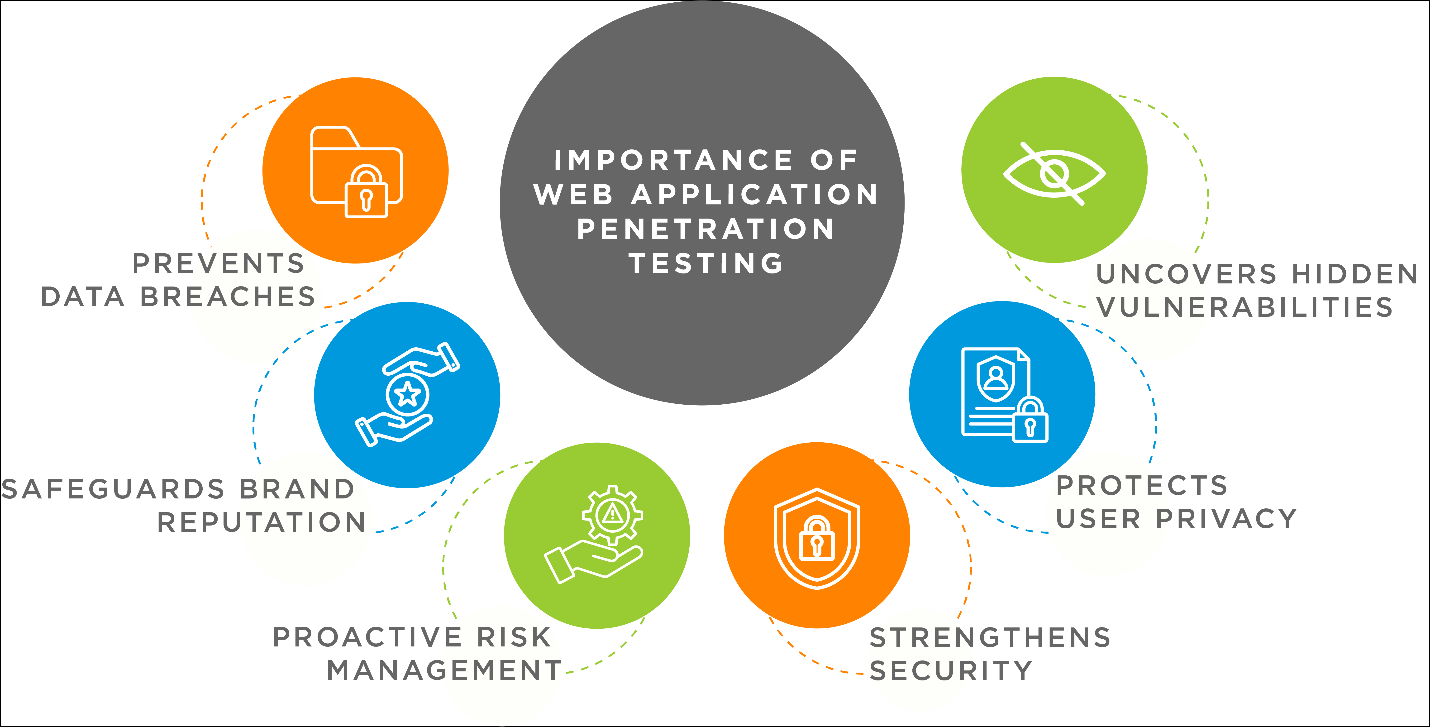
What is the Goal of Web Application Penetration Testing?
Keeping a website secure is important in industries like e-commerce, online banking, healthcare, billing, accounting, and payroll software. Web application penetration testing plays a vital role in achieving this goal. Web applications often store and transmit sensitive data, making them prime cyber-attack targets. It is important to test a web application throughout development, especially if the web application can be accessed online for the following reasons:
- Protection of Sensitive Data: Web applications handle a vast amount of sensitive information, such as personal data, financial details, and confidential business information. Penetration testing helps identify vulnerabilities that could lead to data breaches, protecting this sensitive data from unauthorized access and exploitation.
- Compliance: Many business industries have regulatory requirements, such as GDPR, HIPAA, PCI DSS, NIST, and ISO 27001. Regular web app penetration testing ensures compliance with these regulations, helping organizations avoid legal penalties and maintain trust with customers and stakeholders.
- Preventing Financial Loss: Cyberattacks can lead to financial loss through data breaches, service disruptions, and reputation damage. Penetration testing identifies and mitigates security weaknesses before attackers can exploit them, reducing the risk of costly incidents.
- Maintaining Customer Trust: Security breaches can damage a business’s reputation, causing a loss of customer trust and loyalty. Regular penetration tests show a business’s commitment to security and building and maintaining customer trust.
- Improving Security Posture: Penetration testing provides insights into the security weaknesses of web applications, allowing organizations to address these issues proactively. This continuous improvement in security measures helps maintain a strong security posture over time.
- Identifying Security Gaps in Development: Penetration testing during development helps find security flaws early. This allows web developers to fix issues before the website goes live, reducing costs and effort and ensuring better preparation and control.
- Protecting Publicly Exposed Applications: Web applications accessible via the Internet are particularly vulnerable to attacks. Regular penetration tests protect the website against threats and minimize the risk of a successful cyber-attack.
- Ensuring Business Continuity: Security incidents can disrupt business operations, leading to downtime and loss of productivity. Penetration testing helps prevent such disruptions by ensuring web applications are secure and resilient against attacks.
- Adapting to Evolving Threats: The cyber security landscape constantly evolves, with new threats and vulnerabilities emerging regularly. Penetration testing helps organizations avoid these threats by always assessing and improving security controls.
- Comprehensive Risk Management: Penetration testing is critical to a comprehensive risk management strategy. It provides valuable insights into potential security risks, enabling organizations to make informed decisions and allocate resources effectively to mitigate them.
- Identifying Unknown Vulnerabilities: Some weaknesses can slip through the cracks even with the most thorough security protocols. Penetration testing proactively identifies these blind spots, uncovering vulnerabilities that automated tools or routine checks might miss, making the audience feel vigilant and thorough.
- Evaluate Security Policies: Security policies for web and mobile applications are essential, but verifying their effectiveness is equally important. Pen testing examines these policies, testing their effectiveness in real-world scenarios. This process helps ensure that theoretical defenses hold up under actual attack conditions.
- Public Target: Attackers often first target a company’s digital side, including its firewalls, routers, and DNS systems. Web app pen testing focuses on finding and addressing weak spots in a website’s code to ensure it can defend against hackers.
- Uncovering Data Theft Loopholes: Data is a prime target for cybercriminals. A web app pen test looks for vulnerabilities that could lead to data theft, such as insecure data transmission, improper storage, and other exploitable weaknesses.
- Identifying the Weakest Link: Attackers often look for the path of least resistance. Pen testing helps pinpoint a system’s most vulnerable aspects, which could serve as a gateway for broader attacks. Understanding these weak points allows for targeted defense strengthening.
Over the past 15 years of pen testing web and mobile applications, we have learned how to make them secure. Contact us for a quote for penetration testing services from our cyber security experts.
Types of Web Application Penetration Tests
Tanner Security can divide a web app pen test into different types of tests, and each test will focus on other parts of web security. Each of these tests attempts to identify vulnerabilities that attackers could potentially exploit. Below is a list of the various types of penetration tests tailored explicitly for web applications:

Black Box Testing
- Description: A black box pen test has no prior knowledge of the application’s internal workings. This approach simulates an external cyber-attack and focuses on identifying exploitable vulnerabilities from the outside without any insider information.
- Purpose: Useful for testing the application’s external controls and understanding how an outsider might attempt to breach the system.
White Box Testing
- Description: A white box penetration test gives the pen tester access to the website’s source code, architecture diagrams, and credentials.
- Purpose: This test provides a comprehensive examination of the application for vulnerabilities, including those that are difficult to identify.
- Description: Gray box pen testing is a hybrid approach that offers the tester partial knowledge of the application’s internals. This test may include some access to the architecture and protocols but not the complete source code.
- Purpose: It combines the in-depth test of white box pen test with the realistic perspective of a black box test, offering a comprehensive and cost-effective security assessment that instills confidence in the application’s security.
Static Application Security Testing (SAST)
- Description: SAST involves analyzing an application’s source code, byte code, or binaries without executing it.
- Purpose: Designed to identify security flaws at the code level, SAST enables the proactive detection of vulnerabilities early in the development cycle, enhancing the application’s security from the start.
Dynamic Application Security Testing (DAST)
- Description: DAST focuses on testing an application during its execution, simulating attacks against a running application.
- Purpose: Effective for identifying runtime and environment-related vulnerabilities, such as login and session management.
Interactive Application Security Testing (IAST)
- Description: IAST combines elements of both SAST and DAST, analyzing the application during runtime.
- Purpose: IAST helps show how data moves through the website and how issues are used, giving a clear view of the application’s security.
- Description: APIs usually have an essential function in web applications; an API penetration test explicitly targets the security of web APIs.
- Purpose: Involves testing methods, data handling, login mechanisms, and how APIs interact with other application components.
Each web application penetration test offers unique insights into a web application’s security vulnerabilities. By combining these testing approaches, organizations can assess their web application’s security, uncovering and mitigating potential vulnerabilities to prevent cyber-attacks.
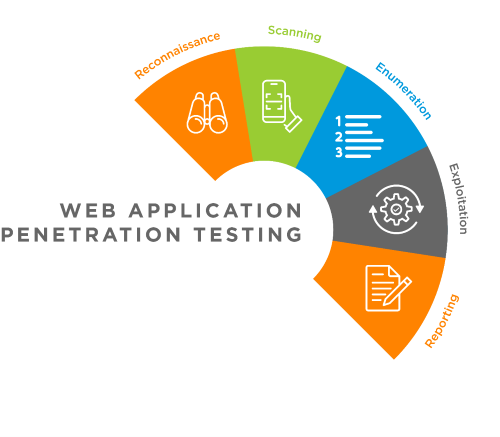
Web Application Penetration Testing Methodology
Web Application Penetration Tests follow a structured approach to identify and exploit vulnerabilities within web applications. This methodology assesses the security of web applications by simulating attacks that cybercriminals might use. Below is an overview of the typical phases we use in our web app pen testing methodology:
Planning and Reconnaissance
- Identify Scope: Define the scope and objectives of the penetration test, including which applications and functionalities we will test.
- Information Gathering: Collect as much information as possible about the target application and its environment. This phase includes understanding the application’s technology stack, mapping out the application, and identifying potential entry points. Tanner Security uses the following tools and techniques in this phase:
- Passive Reconnaissance: Leverage search engines, social media, and public sources for information on the organization, its employees, and potential security gaps.
- Active Reconnaissance: We use tools (Nmap, Wireshark, Burpsuite, and automated web crawlers) to map out the application before testing.
- Scanning
- Automated Scanning: We use tools like Nessus to scan the web application for known vulnerabilities, outdated software versions, poorly written code, and common security issues.
- Manual Scan: We will inspect the application for logical vulnerabilities that automated tools might miss. This phase involves examining the application’s behavior, identifying user roles, and understanding data flow.
Vulnerability Analysis
- Identify Vulnerabilities: Review the automated and manual scanning results to identify potential vulnerabilities within the application.
- Risk Assessment: Assess the severity and potential impact of identified vulnerabilities. This phase will help to prioritize which vulnerabilities to exploit first.
Exploitation
- Exploit Vulnerabilities: We will then exploit each identified vulnerability to determine whether a hacker can gain unauthorized access or engage in other malicious activities. This step verifies whether the vulnerabilities are exploitable in real-world attack scenarios.
- Advanced Exploitation Techniques: Sometimes, we use advanced methods to gain deeper access and show the full impact of a security issue.
Post-Exploitation
- Determine Impact: Once we gain access to a web application, we verify what data can be accessed, the level of control we can get over the system, and how hackers could use the issue to gain more access.
- Persistence: Tanner Security will check for access to show how an attacker could stay unseen on the website for a long time.
Reporting
- Compile Findings: Document all findings, including the vulnerabilities discovered, the exploitation process, and the potential impact.
- Recommendations: Provide detailed recommendations for mitigating the identified vulnerabilities, prioritized by their risk level.
- Report Delivery: Deliver a comprehensive report to stakeholders, outlining the vulnerabilities, evidence of exploitation, and recommendations for security enhancements.
Re-Testing
- Verification: After the client has mitigated the vulnerabilities, we verify the effectiveness of their work through re-testing. The client’s active participation in this phase is crucial for ensuring the security of their web application.
- Continuous Assessment: We strongly recommend doing web application penetration tests regularly, not just once, to ensure ongoing security as the application changes. This continuous approach to testing provides a robust defense against evolving cyber threats.
Our methodology involves a thorough assessment of a web application’s security. We identify all the issues that attackers and cybercriminals could use and give the client insights for improving the application’s security.

Web Application Penetration Testing Tools
Tools used in a web application penetration testing project are vital to any business’s security strategy. These tools simulate attacks on a web application to find vulnerabilities and check how well the defenses work. Below is a list of the tools we regularly use on our web application penetration tests:
- Purpose: Vulnerability Assessment
- Features: Identifies vulnerabilities, configuration problems, and presence of malware.
- Usage: Great for reconnaissance, though not designed for executing exploitations.
- Purpose: To review the network protocol
- Features: Captures and reviews live traffic, examines protocols in detail, and exports data in formats like XML and CSV.
- Usage: Ideal for reviewing network communications to identify potential security issues.
- Purpose: SQL Injection Detection and Exploitation
- Features: Automates the detection and exploitation of SQL injection vulnerabilities.
- Usage: Efficient for quickly identifying and exploiting SQL injection flaws in web applications.
- Purpose: Password Cracking
- Features: Performs dictionary attacks, brute-force attacks, and hybrid combinations to crack password hashes.
- Usage: Analyzes password hashes and reveals cracked passwords, aiding in password security assessments.
- Purpose: Comprehensive Web Application Security Testing
- Features: Includes tools for all testing phases of a web app pen test, like an Intruder for fuzzing, a Repeater for testing requests, and a Sequencer for finding patterns.
- Usage: This is an all-in-one platform for in-depth security testing of web applications.
- Purpose: Network Discovery and Security Auditing
- Features: It scans and provides basic information on a target website, with a scripting engine to detect and exploit issues.
- Usage: We use Nmap for reconnaissance and identifying network security flaws.
- Purpose: Exploit Development and Framework
- Features: It allows the creation of custom tools for specific tasks and the selection and configuration of exploits, payloads, and encoding schemes.
- Usage: Versatile framework for developing and executing exploits against target systems.
- Purpose: Wireless Network Security Testing
- Features: Cracks WEP/WPA/WPA2 keys, identifies unsecured networks, cracks weak Wi-Fi passwords, and decrypts traffic on encrypted networks.
- Usage: Essential for assessing the security of wireless networks and identifying vulnerabilities.
These tools offer a comprehensive suite for penetration testing, allowing security professionals to uncover and address vulnerabilities within web applications. By integrating these tools into their security strategy, organizations can enhance their defenses against potential cyber-attacks.
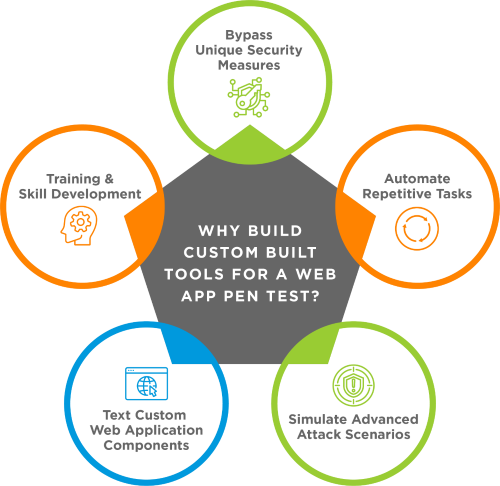
Custom Developed Web App Pen Testing Tools
Security professionals and organizations should not overlook the power of custom-developed web application penetration testing tools. These tools are used for specific testing requirements, allowing you to address specific vulnerabilities and gain insights that other tools often miss. This control over your security posture can significantly enhance your cyber security:
Targeted Vulnerability Assessment
- Our custom tools are precision instruments honed to focus on specific vulnerabilities relevant to a web application or industry. For example, we have built tools that can identify vulnerabilities in custom protocols or login frameworks, providing a level of reassurance and security that off-the-shelf tools cannot match.
Bypassing Unique Security Measures
- Unlike standard tools, our custom-developed tools are adaptable to unique security measures. They can navigate these measures, more accurately assessing an application’s security. This ensures that your specific security needs are being met.
Automating Repetitive Tasks
- We use Python scripts to automate repetitive tasks specific to a particular application or environment. This code can save our team time and effort, allowing us to focus on more complex aspects of a penetration test.
Simulating Advanced Attack Scenarios
- Our custom-built tools can simulate various advanced and sophisticated attack scenarios. These can include complex multi-step attacks, chaining vulnerabilities, or specific attack vectors that regular tools cannot cover.
Testing Custom Web Application Components
- Many web applications have custom-built components that require specialized testing. These can include unique APIs, third-party integrations, or specialized user interactions. For example, we might develop a tool to test the security of a web application’s custom API to communicate with a third-party service.
Compliance and Regulatory Testing
- Organizations subject to industry-specific regulations may require custom tools to ensure compliance with specific security standards.
Real-Time Monitoring and Reporting
- Our web app pen testing tools work with other monitoring and reporting tools to provide ongoing feedback on the web application’s security. These tools can help organizations quickly identify and respond to emerging threats.
Enhanced Accuracy and Coverage
- Custom-built tools identify false positives and negatives, leading to more accurate and thorough web application penetration tests. The tools test will ensure the web application’s critical areas are safe.
Integration with Existing Security Infrastructure
- Custom-developed tools integrate with a business’s security environment, including SIEM systems, threat intelligence platforms, and incident response workflows.
Training and Skill Development
- We build and use tools for training, helping our team practice and improve their skills in identifying and exploiting vulnerabilities. This training can enhance the overall effectiveness of the business’s security efforts.

Custom-built web application penetration testing tools help organizations understand their security, find and fix unique vulnerabilities, and improve overall cyber security.
Penetration Testing Certifications
While penetration testing seems simple, a career in this field requires specific certifications. Below is a list of the certifications that would be required to fine toon your skills in web application pen testing:
Foundational Certifications
- Overview: This entry-level certification establishes basic knowledge in penetration testing methodology, vulnerability scanning, legal aspects, and report writing.
- Topics Covered: Penetration testing planning, scoping, information gathering, vulnerability identification, and reporting.
- Ideal For: Beginners seeking to enter the field of penetration testing.
EC-Council Certified Ethical Hacker (CEH)
- Overview: This vendor-neutral certification covers ethical hacking methodologies, tools, and techniques across various IT systems, including web applications.
- Topics Covered: Footprinting, scanning networks, scan, system hacking, malware threats, and cryptography.
- Ideal For: IT professionals looking to expand their knowledge in ethical hacking.
Intermediate Certifications
Offensive Security Certified Professional (OSCP)
- Overview: This hands-on certification emphasizes practical web application penetration testing skills through a real-world lab environment simulation.
- Topics Covered: Exploitation, privilege escalation, buffer overflows, web application vulnerabilities, and report writing.
- Ideal For: Professionals with foundational knowledge looking to gain practical, hands-on experience.
Certified Ethical Hacker Practical (e|PH)
- Overview: This builds upon CEH knowledge through a performance-based exam to demonstrate web application penetration testing skills.
- Topics Covered: Advanced hacking techniques, real-world scenarios, and comprehensive penetration testing.
- Ideal For: CEH-certified individuals seeking to validate their practical skills.
GIAC Penetration Tester (GPEN)
- Overview: This certification delves deeper into penetration testing practices, vulnerability analysis, and risk assessment.
- Topics Covered: Penetration testing methodologies, password attacks, wireless attacks, and web application attacks.
- Ideal For: Intermediate professionals looking to deepen their penetration testing knowledge.
Advanced Certifications
Certified Penetration Tester (CPT)
- Overview: This vendor-neutral certification emphasizes advanced penetration testing skills across various IT systems, requiring strong technical knowledge and experience.
- Topics Covered: Advanced network and system attacks, exploitation techniques, and in-depth penetration testing strategies.
- Ideal For: Experienced professionals aiming to master penetration testing techniques.
Certified Expert Penetration Tester (CEPT)
- Overview: This certification demands in-depth expertise in penetration testing across various systems, including web applications.
- Topics Covered: Advanced exploitation, malware analysis, reverse engineering, and complex penetration testing scenarios.
- Ideal For: Experts seeking to demonstrate their extensive penetration testing capabilities.
GIAC Exploit Researcher and Advanced Penetration Tester (GXPN)
- Overview: This certification focuses on advanced exploitation techniques, custom exploit development, and in-depth research skills.
- Topics Covered: Exploit development, advanced network attacks, application security, and vulnerability research.
- Ideal For: Professionals passionate about exploit development and advanced penetration testing.
Specialized Certifications
Certified Mobile and Web Application Penetration Tester (CMWAPT)
- Overview: This certification focuses on vulnerabilities specific to mobile and web applications, emphasizing mobile app security testing principles.
- Topics Covered: Mobile app vulnerabilities, web app security testing, and secure coding practices.
- Ideal For: Professionals specializing in mobile and web application security.
GIAC Certified Web Application Penetration Tester (GWAPT)
- Overview: This certification highlights advanced web application penetration testing skills and covers secure coding practices for developers.
- Topics Covered: Web application security, vulnerability assessment, and secure development practices.
- Ideal For: Web developers and security professionals focusing on web application security.
Licensed Penetration Tester Master (LPT) Certification
- Overview: This rigorous two-year program is designed for seasoned professionals seeking additional penetration testing and network security knowledge. It emphasizes practical experience through projects and labs.
- Topics Covered: Advanced penetration testing, network security, ethical hacking, and real-world attack simulations.
- Ideal For: Experienced penetration testers aiming for the highest expertise and recognition in the field.
These certifications provide a structured path for professionals at various levels of expertise to enhance their skills and knowledge in penetration testing, ensuring they are well-equipped to identify and mitigate security vulnerabilities in web applications and other IT systems.
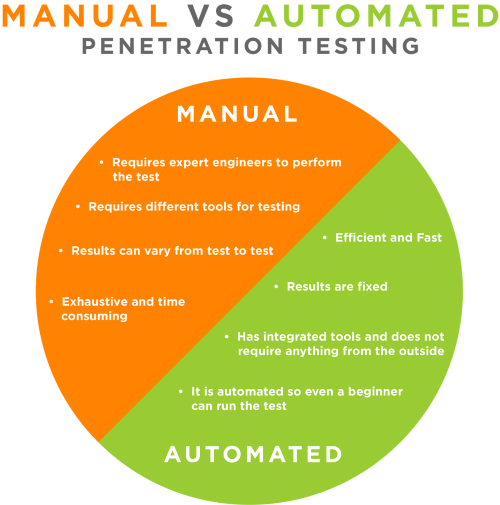
Automated vs. Manual Web App Pen Testing
A web application penetration test is crucial for identifying and mitigating security vulnerabilities. Understanding their strengths and weaknesses is important when deciding between automated and manual penetration tests.
Automated Penetration Test
Automated penetration tests involve using tools to scan systems, identify vulnerabilities, and simulate attacks. Below is an overview of its characteristics:
- Speed and Efficiency: Automated tools can quickly scan large amounts of code and systems, identifying a wide range of vulnerabilities in a short time.
- Coverage: They can efficiently cover known vulnerabilities and common attack vectors, providing a broad security posture assessment.
- Cost-Effectiveness: Automated testing requires less time to complete the test and can be more cost-effective.
- Limitations: Automated tools may generate false positives, reporting vulnerabilities that do not exist. They will also miss all the complex vulnerabilities that require manual inspection and exploitation.
Manual Penetration Test
Manual penetration testing relies on human expertise to identify and exploit vulnerabilities through hands-on testing. Here are its key aspects:
- Thoroughness: Manual testing allows for a deeper, more thorough examination of systems, uncovering complex vulnerabilities and logic flaws that automated tools may overlook.
- Flexibility and Creativity: Skilled testers can adapt their approach, think creatively, and simulate real-world attack scenarios that automated tools cannot replicate.
- Accuracy: Manual testing reduces false positives by verifying vulnerabilities through human judgment and validation.
- Time and Resources: A manual test requires more time due to its labor-intensive nature and dependency on skilled professionals.
Combining Automated and Manual Approaches
Almost all of our tests combine both automated and manual penetration testing approaches:
- Comprehensive Coverage: Automated tools can quickly provide broad coverage, identifying low-hanging fruit and publicly available vulnerabilities. Manual testing then validates and explores deeper, identifying critical vulnerabilities that automated scans may miss.
- Risk Rank: Manual testing helps prioritize vulnerabilities based on potential impact and risk.
- Continuous Improvement: Regular automated scans ensure ongoing monitoring and detection of new vulnerabilities, while periodic manual testing keeps security measures robust and current.
Choosing between automated and manual penetration testing depends on the web application’s complexity, available resources, and the depth of assessment needed. Combining both methods often provides the most effective and thorough evaluation of a web application’s security.
Contact Us
Web applications have transformed how we conduct business, work, interact socially, and manage information. They offer convenience, cost-effectiveness, and significant value. However, their exposure to the Internet also exposes them to potential cyber threats. Even the most advanced web applications can have vulnerabilities in their design and configuration that malicious actors can exploit.Why Choose Tanner Security for Web Application Penetration Testing?
At Tanner Security, we have a proven track record of conducting over 500 web application penetration tests last year. Our cyber security team combines expertise with a proactive approach to deliver thorough assessments and actionable insights.
Partner with Tanner Security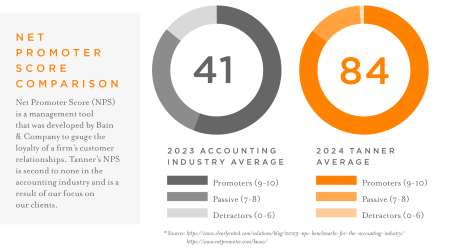
When you partner with Tanner Security, you gain a trusted ally in your cyber security journey. Whether launching a new web application, upgrading existing systems, or ensuring regulatory compliance, we are here to help. Our web app pen testing services address your security needs and will give you peace of mind against cyber threats.
Contact us today to schedule a meeting and learn how Tanner Security can help you meet your cyber security goals.
Let’s work together to safeguard your systems and maintain trust in a data-driven world.