Guide to ISO 27001 Audit and Certification
ISO 27001 Audit Process
Table of Contents
- Introduction
- Step One: Create a Plan
- Step Two: Define the Scope of your ISMS
- Step Three: Perform an ISO 27001 Risk Assessment and Gap Assessment
- Step Four: Design and Implement Policies and Controls
- Step Five: Complete Employee Training
- Step Six: Document and Collect Evidence
- Step Seven: Complete an ISO 27001 Certification Audit
- Step Eight: Maintain Continuous ISO 27001 Compliance
- ISO 27001 Certification Price
Introduction
ISO 27001 certification, though rigorous, provides a few benefits to your organization. These include improved efficiency, enhanced customer trust, and a competitive advantage. Getting ISO 27001 certified is not just a good journey; it’s an opportunity to grow and improve your business. The potential benefits are significant and can lead to a brighter future for your organization.
Starting the ISO 27001 journey involves setting up policies and controls for data security, risk management, and employee training. This guide will walk you through each step to ensure you’re fully prepared.
Getting ISO 27001 certificated is manageable. The process will ensure your business’s information security management system (ISMS) meets the required standards. We’ve created a step-by-step guide to give you confidence and help you prepare for certification. Rest assured, you can successfully navigate this process with the proper guidance.
Certification process phases
To achieve ISO 27001 certification, you must undergo a series of audits. Here’s what you can expect to prepare for and complete your certification.
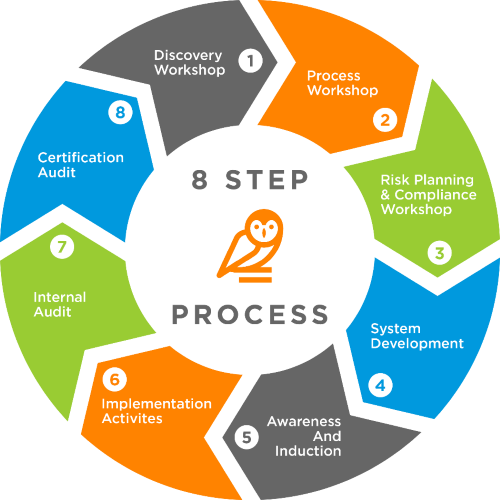
Step One – Create a Plan
Understand the Requirements
- Become familiar with the ISO 27001 framework: Read and understand the ISO 27001 standard, including Annex A, which lists the security controls.
- Management Support: Make sure top management is committed to the certification process and understands its importance.
Who will oversee the certification process, set expectations, and manage milestones within your organization? How will you get buy-in from company leadership? If you’re new to ISO/IEC 27001:2022 or find the process hard, consider hiring an ISO 27001 consultant to help you through this process.
Understanding ISO 27001 and its 114 controls is crucial for successful certification. This knowledge is key to navigating the process. We’re here to help you master these controls, ensuring you can confidently manage your certification journey.
Overseeing the ISO 27001 Certification Process
Appointing a Project Leader
- Information Security Manager (ISM): An Information Security Manager or a similar role will typically oversee the ISO 27001 certification process. This person will be responsible for setting expectations, managing milestones, and ensuring the project stays on track. Their responsibilities include coordinating with different departments, ensuring compliance with the standard, and managing the documentation process.
- Project Team: Get a project team together from all of the key departments (e.g., IT, HR, legal, operations) to give input and support the process.
Responsibilities of the Project Leader
When pursuing ISO 27001 certification, the Project Leader will develop a detailed project plan with clear milestones and deadlines. Regular communication with stakeholders, including top management, is crucial to inform everyone of progress. Enough resources (time, budget, and personnel) must be given to support this process.
The Project Leader will also oversee the creation and maintenance of required documentation. Finally, they will ensure that all employees receive appropriate training and awareness sessions to effectively implement and sustain the Information Security Management System (ISMS).
Getting Buy-In from Company Leadership
Presenting the benefits of ISO 27001 certification includes:
- Emphasizing how it helps manage and mitigate information security risks.
- Enhancing the company’s reputation.
- Providing a competitive edge.
Certification also highlights the importance of meeting regulatory and contractual requirements, increasing customer confidence and trust in the organization. To ensure executive support, appoint an executive sponsor to lead the project and maintain leadership backing. The project lead should update the leadership team on progress, challenges, and successes and show the return on investment (ROI) through better security, reduced risk, and potential new business opportunities.

Considering an ISO 27001 Consultant
When should a company use an ISO 27001 consultant?
An ISO 27001 consultant is recommended when your business needs additional internal experience, has a complex IT environment, or needs to be certified quickly. A consultant provides expert guidance and advice throughout the certification process, helping to streamline implementation and avoid common pitfalls. They can customize the Information Security Management System (ISMS) to fit your business’s specific needs and offer training or support to ensure your staff is well-prepared.
Understanding ISO 27001 and Its 114 Controls
The Structure of ISO 27001
- Clause 4-10: These clauses cover the management system requirements, including context, leadership, planning, support, operation, performance evaluation, and improvement.
- Annex A: Contains 14 domains with 114 controls, which provide the framework for identifying and mitigating information security risks. These controls cover many aspects, from information security policies to business continuity management, ensuring a thorough approach to information security.

Key Domains and Controls
- Annex 5: Information Security Policies: Policies for information security.
- Annex 6: Organization of Information Security: Internal organization, mobile devices, and teleworking.
- Annex 7: Human Resource Security: Employee screening, training, and discipline processes.
- Annex 8: Asset Management: Inventory of assets, ownership, acceptable use.
- Annex 9: Access Control: User access management, user responsibilities, system and application access control.
- Annex 10: Cryptography: Encryption and key management.
- Annex 11: Physical and Environmental Security: Secure areas equipment security.
- Annex 12: Operations Security: Technical operation procedures, malware protection, backup.
- Annex 13: Communications Security: Network security management, information transfer.
- Annex 14: System Acquisition, Development, and Maintenance: Security requirements, secure development policy.
- Annex 15: Supplier Relationships: Supplier security policy, managing changes to supplier services.
- Annex 16: Information Security Incident Management: Incident management responsibilities and procedures.
- Annex 17: Information Security Aspects of Business Continuity Management: Continuity planning, implementing continuity plans.
- Annex 18: Compliance: Legal and regulatory compliance, audit considerations.
Navigating the Controls
- Risk-Based Approach: Identify relevant controls based on your ISO 27001 risk assessment.
- Implementation Guidance: Use ISO 27002 for detailed guidance on implementing the controls.
- Documentation: Maintain thorough documentation to demonstrate compliance during the audit.
By understanding the ISO standard, managing the process, and using professional guidance, your business can get ISO 27001 certified and enjoy the benefits of improved information security and business resilience.

Step Two – Define the Scope of Your ISMS
Defining the scope of your ISMS is a key step in the ISO 27001 certification process. The scope sets the boundaries of the ISMS and its use within your business, specifying the parts that will be covered and how information security will be managed in those areas.
Steps to Define the Scope of Your ISMS
- Understand the Context of the Organization
- Internal Context: Consider internal factors such as organizational structure, culture, information systems, and existing security measures.
- External Context: Consider external factors such as regulatory requirements, customer expectations, market conditions, and technological changes.
- Identify Interested Parties and Their Requirements
- Stakeholders: Identify key stakeholders, including employees, customers, suppliers, regulators, and partners.
- Requirements: Understand and document these stakeholders’ information security requirements and expectations.
- Determine the Boundaries
- Physical: Define the physical locations (e.g., offices, data centers) included in the scope.
- Business: Define the company’s covered parts (e.g., departments, units).
- Technical: Identify the technical systems, applications, and data types that will be included.
- Consider the ISMS Objectives
- Objectives and Goals: Align the scope with your ISMS’s objectives and goals. Ensure that the scope supports your business’s overall information security strategy.
- Document the Scope
- Clear Definition: Provide a clear and concise definition of the scope, outlining what is included and excluded.
- Scope Statement: Create a formal statement that business leaders can include in your ISMS and review.
- Review and Approve
- Management Review: Present the scope to top management for review and approval.
- Stakeholder Communication: Communicate the approved scope to all relevant stakeholders to ensure understanding and buy-in.
Policies and Procedures
- Develop Policies and Procedures: Create and document information security policies and procedures that align with ISO 27001 requirements.
- Implement Controls: Implement the necessary security controls as specified in Annex A to address identified risks.
Training and Awareness
- Employee Training: Conduct training programs to ensure employees know their roles and responsibilities within the ISMS.
Each business is unique and handles various types of data. Before developing your ISMS, you must decide what information needs protection.
For some businesses, the ISMS scope covers the entire organization, while for others, it might focus on a specific department or system.
Your team should decide what to include in the scope statement of your ISO 27001 certificate.
“What service, product, process, or platform do our customers most want to see covered by our ISO 27001 certificate?”

Step Three: Perform an ISO 27001 Risk Assessment and Gap Assessment
ISO 27001 Gap Assessment
- Perform a Gap Assessment: Identify the gaps between your current security posture and the requirements of ISO 27001.
- Risk Assessment: Conduct a risk assessment to identify and evaluate risks to your information assets.
A formal risk assessment and gap assessment are required for ISO 27001 compliance. The results must be documented.
To start, consider your baseline for security. What legal, regulatory, or contractual obligations must your company perform?
Startups and businesses that need an internal compliance team normally hire an ISO 27001 consultant to help perform a gap assessment and create a plan to fix controls. ISO 27001 consulting services with experience working with companies like yours can provide expert guidance to help you meet compliance requirements and establish best practices that strengthen your overall security posture.
ISO 27001 Risk Assessment
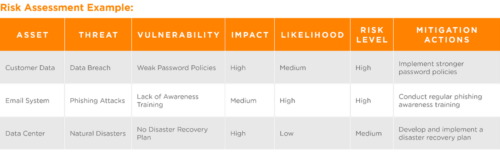
A risk assessment is a process for identifying, evaluating, and managing risks to a business’s information security. This step is essential for understanding the threats and risks that could impact information technology assets.
Steps to Perform an ISO 27001 Risk Assessment:
- Identify IT Assets: List all IT assets, including hardware, software, data, and personnel.
- Identify Threats: Determine each asset’s potential threats (e.g., cyber-attacks, natural disasters) and risks (e.g., outdated software, lack of training).
- Assess Impact and Likelihood: Evaluate each threat’s potential impact and likelihood. This assessment can use qualitative or quantitative methods.
- Determine Risk Levels: Calculate each threat’s risk level using a risk matrix to evaluate both impact and likelihood.
- Prioritize Risks: Rank the risks based on their risk levels to prioritize which must be addressed first.
- Mitigate Risks: Develop and implement risk treatment plans to mitigate the identified risks. The plan could involve implementing new controls, improving controls, or accepting the risk if it is within an acceptable level.
- Document and Review: Document the risk assessment process and findings. Regularly review and update the risk assessment to ensure it remains current.
ISO 27001 Gap Assessment
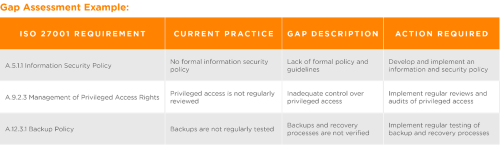
A gap assessment identifies the differences between your current information security practices and the requirements of ISO 27001 and helps you determine what needs to be addressed.
Steps to Perform a Gap Assessment:
- Review ISO 27001 Requirements: It is important to familiarize yourself with the ISO 27001 standards and the controls outlined in Annex A.
- Assess Current Practices: Evaluate your existing information security practices, policies, and controls against the ISO 27001 requirements.
- Identify Gaps: Identify areas where your current practices do not meet ISO 27001 requirements.
- Document Findings: Document the gaps and identify the requirements, current state, and required changes.
- Develop an Action Plan: Create an action plan to address the identified gaps, including timelines and responsibilities.
Combining Risk and Gap Assessments
Using the results from your ISO 27001 risk assessment and gap assessment will give you a clear understanding of your current information security status and what needs to be done to achieve ISO 27001 certification.

By performing a thorough risk and gap assessment, you can create a plan to address the areas that need improvement, preparing your business for a successful ISO 27001 certification audit.

Step Four: Design and Implement Policies and Controls
Designing and implementing ISO 27001 policies and procedures is critical to achieving ISO certification. This step involves creating comprehensive information security policies and implementing the necessary controls to mitigate identified risks and close gaps.
Controls for Business Operations
- Implement Controls: Put your documented policies and controls into practice.
- Record Keeping: Maintain records to provide evidence of compliance with the standard.
ISO 27001 Internal Audit
- Conduct Internal Audits: Regularly perform internal audits to check the effectiveness of your ISMS and ensure compliance with ISO 27001 standards.
Steps to Design Information Security Policies
Your ISO 27001 auditor will review your decisions on each identified risk during your audit. You must provide a “Statement of Applicability” and a “Risk Treatment Plan” as part of your audit evidence.
The “Statement of Applicability” outlines which ISO 27001 controls and policies apply to your business and is one of the first documents your auditor will review.
- Identify Required Policies: Review the ISO 27001 standard and Annex A controls to determine the necessary policies.
- Engage Stakeholders: Involve relevant stakeholders in the policy design process to ensure policies are practical and aligned with organizational needs. Stakeholders can include IT, HR, legal, operations, and executive management.
- Draft Policies: Write clear, concise, and comprehensive policies. Ensure policies include purpose, scope, responsibilities, and specific procedures or guidelines.
- Review and Approve: Conduct a review process and incorporate feedback from stakeholders. Obtain approval from top management to ensure buy-in and enforcement.
- Communicate and Distribute: Communicate the policies to all employees and ensure they are easily accessible, such as via an internal intranet or shared folder.
- ISO 27001 Information Security Policy
- ISO 27001 Access Control Policy
- ISO 27001 Risk Management Policy
- ISO 27001 Incident Response Policy
- ISO 27001 Business Continuity Policy
The Risk Treatment Plan is crucial for ISO 27001 certification. It details how your organization will address the risks identified in the risk assessment.
The ISO 27001 standard outlines four actions to manage risks:
- Modify: Implement controls to reduce the likelihood of the risk.
- Avoid: Prevent situations where the risk could occur.
- Share: Transfer the risk to a third party, such as through outsourcing or insurance.
- Accept: Accept the risk if the cost of addressing it exceeds the potential damage.
After creating the Risk Treatment Plan, you must implement policies and controls. These should include security best practices, like requiring multi-factor authentication and locking devices when not in use.

Step Five: Complete Employee Training
ISO 27001 requires all employees to receive information security training. This is not just a requirement but acknowledges each team member’s important role in maintaining compliance.
Employee training is vital for ISO 27001 compliance. It ensures everyone understands their responsibilities and contributes effectively to the Information Security Management System (ISMS).
Employee Training Objectives
- Awareness: Increase awareness of information security risks and the importance of ISO 27001.
- Roles and Responsibilities: Clearly define and communicate each employee’s role in protecting information.
- Policies and Procedures: Ensure employees understand and adhere to the business’s information security policies and procedures.
- Skills Development: Provide necessary skills and knowledge to manage and respond to security incidents.
Steps to Implement Employee Training
- Develop a Training Plan
- Identify Training Needs: Determine the specific training needs for different organizational roles.
- Define Objectives: Set clear objectives for what the training should achieve.
- Create a Training Schedule: Develop a schedule that includes initial training and regular refresher courses.
- Design Training Programs
- Content Development: Create training materials that cover the business’s information security policies, procedures, and controls. Use various formats such as presentations, e-learning modules, videos, and interactive sessions.
- Role-Specific Training: Tailor training content to different employees’ specific roles and responsibilities. For example, IT staff may need more technical training, while general staff require broader awareness training.
- Deliver Training
- Initial Training Sessions: Conduct initial training sessions for all employees. Use in-person and online formats to ensure employees can access the information.
- Ongoing Training: Regular training sessions are required to inform employees about information security, update them on new threats, and review controls.
- Evaluate and Improve
- Feedback Mechanisms: Collect feedback from employees on the effectiveness of the training sessions. Use surveys, quizzes, and interactive discussions to gauge understanding.
- Continuous Improvement: Regularly review and update training materials based on feedback and changes in the information security landscape.
- Document Training
Training Records: Maintain detailed records of all training sessions, including attendance, content covered, and assessment results. This documentation is crucial for demonstrating compliance during the ISO 27001 audit.

Step Six: Document and Collect Evidence
Documenting your Information Security Management System (ISMS) and collecting evidence of its implementation and effectiveness are critical steps in achieving ISO 27001 certification. This documentation proves compliance and provides a clear, auditable trail for external auditors.
Management Review
- Management Review Meetings: Hold periodic management review meetings to evaluate the performance of the ISMS.
Continual Improvement
- Address Non-conformities: Identify, document, and address non-conformities through corrective actions.
- Monitor and Review: Monitor and review the ISMS to identify opportunities for improvement.
To get certified, you must show your ISO 27001 auditor that you’ve created effective policies and controls that function as required.
Collecting and organizing all this evidence can be extremely time-consuming. Software for ISO 27001 can eliminate hundreds of hours of busy work by collecting this evidence for you.
Collecting Evidence
- Policy and Procedure Documentation
- Ensure all policies and procedures are documented, approved, and communicated to relevant stakeholders.
- ISO 27001 Implementation Records
- Maintain records showing the implementation of policies and controls, such as configuration files, system logs, and access control lists.
- Risk Management Evidence
- Document risk assessments, treatment plans, and risk acceptance or mitigation decisions.
- Training and Awareness Programs
- Keep records of training sessions, attendance lists, training materials, and employee feedback.
- Monitoring and Audit Logs
- Collect logs and records from security monitoring tools, system audits, and access controls.
- Incident Response Records
- Document incidents, responses, investigations, and outcomes to demonstrate the effectiveness of incident management procedures.
- Review and Improvement Records
- Keep records of management review meetings, internal audits, and corrective actions.
Tips for Effective Documentation
- Consistency
- Use standardized templates for all documentation to ensure consistency and ease of review.
- Version Control
- Implement a version control system to track document changes and ensure the latest versions are used.
- Access
- Ensure that all documentation is easily accessible to those who need it while maintaining appropriate security controls.
- Clear and Concise Language
- Use clear and concise language to ensure that all stakeholders easily understand documentation.
- Regular Updates
- Regularly review and update documentation to reflect organizational changes, technology, or the threat landscape.
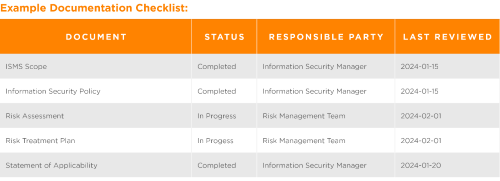
It is essential to document your ISMS and collect evidence of its implementation and effectiveness for ISO 27001 compliance. Maintaining comprehensive, well-organized documentation and regularly updating it demonstrates your business’s commitment to information security and readiness for the certification audit.

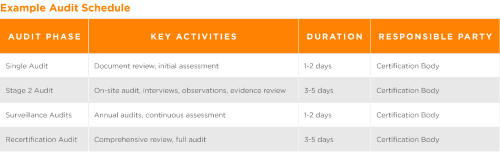
Step Seven: Complete an ISO 27001 Certification Audit
The final step to achieving ISO 27001 certification is the certification audit by an accredited body. This audit checks that your Information Security Management System (ISMS) meets ISO 27001 standards and is properly implemented and maintained.
Phases of the Certification Audit
- Stage 1 Audit (Document Review)
- Stage 2 Audit (Certification Audit)
- Surveillance Audits
- Ongoing Audits
Stage 1 Audit: Document Review
The Stage 1 Audit involves the auditor reviewing your ISMS documentation to ensure it meets ISO 27001 requirements. The auditor usually conducts this stage remotely but may include some on-site visits to verify controls.
Objectives of Stage 1 Audit:
- Confirm that the ISMS documentation is complete and aligns with ISO 27001 requirements.
- Assess the business’s readiness for the Stage 2 Audit.
- Identify and address any significant non-conformities before moving on to Stage 2.
Key Activities:
- Review the ISMS scope, policies, risk assessment, risk treatment plan, and Statement of Applicability (SoA).
- Evaluate the overall design of the ISMS, including objectives, roles and responsibilities, and resources.
- Provide a report outlining any findings and recommendations.
Preparation:
- Ensure that all ISMS documentation is up-to-date and accessible.
- Address any significant non-conformities identified during internal audits.
Stage 2 Audit: Certification Audit
The Stage 2 Audit thoroughly examines your ISMS’s implementation and effectiveness. The auditor conducts this stage on-site and performs interviews, observations, and evidence reviews.
Objectives of Stage 2 Audit:
- The ISO 27001 auditor will verify that the ISMS is fully implemented and working correctly.
- Assess the effectiveness of the ISMS in managing information security risks.
- Confirm that the organization complies with ISO 27001 requirements.
Key Activities:
- Conduct interviews with key personnel to understand their roles and responsibilities in the ISMS.
- Observe the implementation of controls and processes in practice.
- Review evidence of ISMS operation, such as audit logs, incident reports, and monitoring results.
- Evaluate the effectiveness of risk management and treatment processes.
Preparation:
- Ensure all employees know the audit schedule and their roles in the audit process.
- Conduct a final internal audit to identify and address any remaining non-conformities.
- Gather and organize all necessary evidence and documentation.
Surveillance Audits
After obtaining certification, the organization must undergo regular surveillance audits (usually annually) to ensure continued compliance with ISO 27001.
Objectives of Surveillance Audits:
- Verify ongoing compliance with ISO 27001 requirements.
- Ensure continuous improvement of the ISMS.
- Identify and address any new risks or non-conformities.
Key Activities:
- Review updates to the ISMS, including any changes to the scope, policies, and controls.
- Evaluate the effectiveness of corrective and preventive actions taken since the last audit.
- Conduct interviews and observations to ensure ongoing implementation of ISO 27001 and the effectiveness of controls.
Preparation:
- Maintain regular internal audits and management reviews.
- Update and improve the ISMS based on audit findings and changing risks.
Ongoing Audits
You must perform an audit every three years to maintain ISO 27001 certification.
Objectives of Ongoing Audits:
- Confirm continued compliance with ISO 27001 requirements.
- Assess the maturity and continual improvement of the ISMS.
Key Activities:
- Comprehensive review of the ISMS documentation, implementation, and effectiveness.
- Evaluate the business’s ability to manage information security risks over time.
Preparation:
- The auditor will verify the ISMS has been improved and updated.
- Prepare for a full audit similar to the initial Stage 2 Audit.
Tips for a Successful Certification Audit
- Engage Top Management:
- Ensure top management is fully committed and involved in the ISMS.
- Demonstrate their support and involvement with the auditors.
- Communicate with Employees:
- Inform all employees about the audit process and their roles.
- Provide necessary training and support to prepare for the audit.
- Organize Documentation:
- Keep all ISMS documentation well-organized and accessible.
- Ensure that all records are up-to-date and complete.
- Conduct ISO 27001 Internal Audits:
- Regularly perform internal audits to identify and address non-conformities.
- Use the findings to improve the ISMS.
- Address Non-Conformities:
- Promptly address any non-conformities identified during internal audits or the Stage 1 Audit.
- Implement corrective actions and document the process.
- Complete and accessible documentation
- Fully implemented policies and procedures
- Trained staff aware of their roles
- Conducted internal audits and management reviews
- Addressed non-conformities
Step Eight: Maintain Continuous ISO 27001 Compliance
Achieving ISO 27001 certification is a significant milestone, but maintaining compliance is an ongoing process that requires continuous effort and attention. The goal is to ensure that the Information Security Management System (ISMS) is effective and adapts to new risks, regulatory changes, and business needs.
Activities for Continuous Compliance
- Regular Internal Audits
- Management Reviews
- Continuous Risk Management
- Ongoing Training and Awareness
- Incident Management and Response
- Continuous Improvement
- Surveillance Audits
- Documentation and Record-Keeping
- Regular Internal Audits
Purpose:
- Ensure ongoing compliance with ISO 27001 requirements.
- Identify areas for improvement within the ISMS.
Activities:
- Schedule regular internal audits (at least annually).
- Use a risk-based approach to focus on high-risk areas.
- Document findings and corrective actions.
Preparation:
- Develop an internal audit plan and checklist.
- Train internal auditors on ISO 27001 requirements and audit techniques.
- Review previous audit findings and corrective actions.
- Management Reviews
Purpose:
- Evaluate the performance and effectiveness of the ISMS.
- Ensure alignment with business objectives and risk appetite.
Activities:
- Conduct management review meetings at least annually.
- Review key performance indicators (KPIs), audit results, incident reports, and risk assessments.
- Make decisions on necessary changes and improvements.
Preparation:
- Gather relevant data and reports for the review.
- Prepare an agenda and distribute it to participants in advance.
- Document the outcomes and action items from the review meeting.
- Continuous Risk Management
Purpose:
- Identify and mitigate new and emerging risks.
- Ensure the risk treatment plan remains effective and relevant.
Activities:
- Regularly update the risk assessment and risk treatment plan.
- Monitor the effectiveness of implemented controls.
- Address any new risks or changes in the threat landscape.
Preparation:
- Schedule periodic risk assessment reviews.
- Engage relevant stakeholders in the risk management process.
- Use risk management tools and software to streamline the process.
- Ongoing Training and Awareness
Purpose:
- Keep employees informed about information security policies and best practices.
- Ensure that new employees receive the necessary training.
Activities:
- Conduct regular training sessions and awareness campaigns.
- Update training materials to reflect changes in policies and threats.
- Monitor and document training participation and effectiveness.
Preparation:
- Develop a training schedule and materials.
- Use various training methods (e.g., e-learning, workshops, simulations).
- Evaluate training effectiveness through assessments and feedback.
- Incident Management and Response
Purpose:
- Ensure prompt and effective response to security incidents.
- Minimize the impact of incidents on the organization.
Activities:
- Maintain and update incident response procedures.
- Conduct regular incident response drills and simulations.
- Review and analyze incidents to identify root causes and preventive measures.
Preparation:
- Develop an incident response plan and communication strategy.
- Train employees on incident reporting and response procedures.
- Maintain incident logs and investigation records up-to-date.
- Continuous Improvement
Purpose:
- Enhance the ISMS based on audit findings, incident reports, and feedback.
- Foster a culture of constant improvement within the organization.
Activities:
- Implement corrective and preventive actions for identified non-conformities.
- Regularly review and update policies, procedures, and controls.
- Encourage employee feedback and suggestions for improvement.
Preparation:
- Establish a process for tracking and implementing improvements.
- Use tools like the PDCA (Plan-Do-Check-Act) cycle for systematic improvement.
- Communicate improvements and their benefits to employees.
- Surveillance Audits
Purpose:
- Verify ongoing compliance with ISO 27001 requirements.
- Ensure the ISMS continues to be effective and efficient.
Activities:
- Schedule annual surveillance audits with the certification body.
- Prepare for the audits by reviewing and updating documentation and evidence.
- Address any non-conformities identified during the audits.
Preparation:
- Maintain regular communication with the certification body.
- Ensure all documentation and records are current and accessible.
- Conduct internal pre-audit checks to identify potential issues.
- Documentation and Record-Keeping
Purpose:
- Provide evidence of compliance and effective ISMS operation.
- Ensure accountability within the ISMS.
Activities:
- Keep all ISMS documentation up-to-date and well-organized.
- Maintain records of audits, training, incidents, and management reviews.
- Use a document management system to control document versions and access.
Preparation:
-
- Develop and follow a documentation control policy.
- Train employees on the importance of accurate record-keeping.
- Regularly review and archive outdated documents as necessary.

ISO 27001 Certification Price
Determining the cost of ISO 27001 certification can be challenging, as many different factors influence it. The price depends on your business’s size, number of locations, type of data, and whether you use internal resources or hire an ISO 27001 consultant.
The cost of ISO 27001 certification can range as follows:
- Audit Preparation: Up to $40,000
- Certification Audit: $15,000+
- Maintenance and Surveillance: $10,000 annually
Here’s a breakdown of the main cost categories:
- Preparation Costs
- ISO 27001 & 27002 Standards: ~$500 (ISO 27001: ~$250, ISO 27002: ~$350)
- ISO 27001 Consultant: ~$38,000 (Average cost; includes pre-certification phases)
- Phase I: $20,000 (Scope definition, risk assessment, gap assessment)
- Phase II: $18,000 (Fix gaps, ISMS development, audit support)
- Gap Assessment: $8,500
- Penetration Test: ~$8,000 to $20,000 (Pen tests: $6,000-$20,000; Vulnerability assessments: $2,000-$6,500)
- Implementation Costs
- Employee Training: ~$5,000 annually
- Security Software and Tools: Varies
- Lost Productivity: Varies
- Certification Audit Costs
- ISO 27001 Audits: ~$10,000 to $50,000
- Stage 1: Document review
- Stage 2: Process and controls evaluation
- Surveillance Audits: End of years 1 and 2
- Ongoing Audits: End of year 3
Saving on the ISO 27001 Certification Price:
While ISO 27001 certification is a significant investment, compliance automation can reduce costs by increasing efficiency. The certification process is all about continuous improvement. You must keep analyzing and reviewing your ISMS to ensure it operates effectively. But remember, resources and guidelines are available to help you with this ongoing process.