Guide to Network Penetration Testing
NET PEN TESTING
Table of Contents
- Introduction to Network Penetration Testing
- Understanding the Basics of Network Security
- Process of Network Penetration Testing
- Tools & Technologies
- Ethical and Legal Considerations
- Network Penetration Testing – Best Practices
- Learning and Certification Opportunities
- Future of Network Penetration Testing
INTRODUCTION TO NETWORK PENETRATION TESTING
Network penetration testing, or “pen testing,” is a critical cyber security practice. It finds, evaluates, and fixes network vulnerabilities by simulating cyber-attacks. This helps security professionals understand how attackers could exploit weaknesses, maintain strong security, and protect networked systems. This proactive approach is essential for maintaining a robust security posture and ensuring the integrity and confidentiality of networked systems.
Network penetration testing is a methodical process where security experts simulate malicious attacks on a network to uncover vulnerabilities that hackers might exploit. Skilled analysts usually perform penetration testing manually, thinking like attackers. They use tools and techniques to find and fix network security flaws before real attackers can exploit them.
Importance of Network Penetration Testing in Cybersecurity
In today’s digital age, the importance of network penetration testing cannot be overstated. With cyber threats evolving at an unprecedented pace, organizations must be proactive in detecting and mitigating potential security breaches. Penetration testing plays a vital role in this endeavor by:
- Identifying vulnerabilities – Before they can be exploited by malicious actors, preventing unauthorized access, data breaches, and potential financial loss.
- Compliance – Ensuring compliance with regulatory requirements (PCI, ISO 27001, HIPAA, NIST, CIS) that mandate regular security assessments to protect sensitive data.
- Security posture assessment – Providing an empirical understanding of the business’s security posture, allowing for informed decision-making regarding investments in security resources.
Key Objectives and Benefits
The primary objectives of network penetration testing include:
- Vulnerability identification – To locate and document vulnerabilities in the network infrastructure.
- Risk assessment – To evaluate the potential impact and likelihood of exploits on the business’s operations and reputation.
- Security enhancement – To recommend measures to mitigate identified vulnerabilities, thereby strengthening the network’s security.
Regular network penetration tests provide significant benefits, helping organizations improve security, comply with legal and regulatory standards, and maintain stakeholder trust. Here are some of the key benefits:
- Proactive Identification of Vulnerabilities – Regular penetration testing proactively identifies weaknesses in a business’s network before attackers can exploit them. Early detection lets you fix vulnerabilities, lowering the risk of unauthorized access and data breaches.
- Risk Management – Penetration testing identifies and evaluates vulnerabilities, helping organizations understand their risks. This lets them prioritize fixes based on severity and impact, efficiently addressing the most critical issues.
- Compliance with Regulations and Standards – Many industries must follow regulations that require regular security assessments, including penetration testing, to protect sensitive data. Regular testing ensures compliance with PCI DSS, CMMC, ISO 27001, HIPAA, and GDPR standards, helping avoid fines and legal penalties.
- Enhanced Security Measures – Penetration testing offers detailed feedback on the effectiveness of a business’s security measures. This information is critical to strengthening defenses by highlighting areas for improvement, like better security policies, more employee training, or advanced technology.
- Cost Savings – Fixing issues found in a penetration test is usually much cheaper than dealing with the costs of an attack, like data recovery, legal fees, and fines. Regular testing helps avoid these expensive problems.
- Support for Security Investments – Penetration test results can show why investing in security technology and staff is necessary. They help organizations justify spending on improving cyber security by highlighting potential risks and impacts.
- Enhanced Incident Response and Recovery – Regular testing helps organizations improve their incident response plans by identifying potential attack vectors and preparing appropriate mitigation strategies. This readiness can significantly reduce the impact of a security breach and expedite recovery efforts.

In conclusion, network penetration testing is a cornerstone of modern cybersecurity strategies. It enables organizations to identify and address security vulnerabilities, protecting their digital assets against ever-evolving cyber threats. Regular penetration testing helps organizations stay secure, meet regulatory standards, and build trust with clients and stakeholders.
UNDERSTANDING THE BASICS OF NETWORK SECURITY
Network security is a critical aspect of information technology that involves implementing measures to protect data and infrastructure from unauthorized access, misuse, or harm. This section provides an overview of network security, highlights common network vulnerabilities, and describes various types of network attacks, laying the foundation for understanding the importance of robust security practices.
Overview of Network Security
Network security refers to the policies, procedures, and technologies designed to safeguard computer networks and data’s integrity, privacy, and availability. It encompasses a wide range of practices aimed at preventing unauthorized access, cyberattacks, and data breaches. Effective network security manages access to the network, employs multiple layers of defense at the edge and within the network, and protects the usability, reliability, integrity, and safety of the network and data.
Key Components of Network Security:
- Physical Security – Protecting the physical infrastructure against unauthorized access.
- Technical Security – Involves safeguarding data stored on the network or in transit across, into, or out of the network.
- Administrative Controls – Policies and procedures that control user behavior, including how users are logged in and their level of access to network resources.
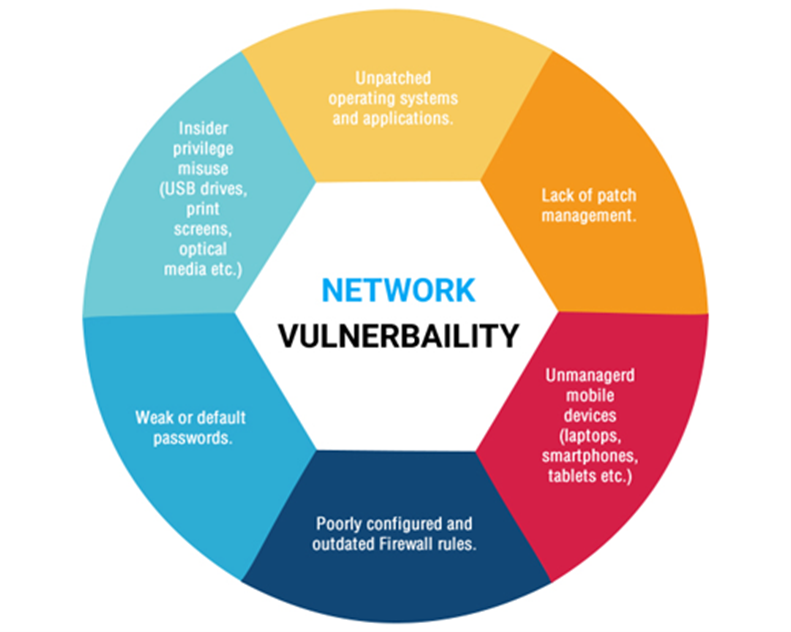
Common Network Vulnerabilities
Network vulnerabilities are weaknesses or flaws attackers can exploit to gain unauthorized access or harm the network. Identifying and mitigating these vulnerabilities is crucial for maintaining network security.
Examples of Common Vulnerabilities:
- Poorly Configured Firewalls- Incorrectly configured firewalls can expose the network to attacks.
- Unpatched Software – Software that hasn’t been updated or patched can contain exploitable vulnerabilities.
- Weak Login Mechanisms – Simple or default passwords make unauthorized access easier.
- Unencrypted Data – Unencrypted data is susceptible to interception and unauthorized access.
- Insufficient Network Segmentation – Lack of segmentation can allow attackers to move laterally within a network easily.
Types of Network Attacks
Network attacks are actions by malicious actors to exploit vulnerabilities, disrupt operations, or gain unauthorized access to network resources. Understanding these attack types is essential for implementing effective defense strategies.
Common Types of Network Attacks
- Man-in-the-Middle (MitM) Attacks – Attackers intercept and possibly alter communications between two parties without their knowledge.
- Phishing and Spear Phishing Attacks – These attacks use deceptive emails or messages to trick users into revealing sensitive information or installing malware.
- SQL Injection – Malicious code is injected into SQL queries to manipulate databases to reveal information.
- Ransomware – Malware that encrypts files on the victim’s system, demanding payment for decryption keys.
- Zero-Day Exploits – Attacks that target unpatched vulnerabilities in software or hardware are known as “zero-day” because developers have zero days to fix the vulnerability since it’s already being exploited.
Network security is complex and needs a multi-layered approach to defend against various vulnerabilities and attacks. By understanding the basics, common vulnerabilities, and types of attacks, organizations can better prepare and implement effective security measures to protect their digital assets.
PROCESS OF NETWORK PENETRATION TESTING
Network penetration testing is a structured approach to identifying and exploiting vulnerabilities within network systems. This process is crucial for enhancing a business’s security posture. Here, we explore the key phases, from pre-engagement interactions to exploitation, highlighting the methodologies and considerations involved at each stage.
Pre-engagement Interactions
Before commencing a penetration test, clear communication between the testing team and the client is essential to define the engagement’s goals, scope, and boundaries.
- Setting Goals and Scope – The objectives of the test are established, including which systems, networks, and applications will be assessed. The scope may vary based on the client’s needs, ranging from a broad assessment of the business’s external network to a focused evaluation of a specific application.
- Legal and Ethical Considerations – Ensuring the penetration test is conducted within legal boundaries is critical. Written permission from the client detailing the agreed-upon scope and methods protects both parties. Ethical guidelines must be followed to ensure that the test does not cause undue harm or disrupt the client’s operations.
Reconnaissance
In reconnaissance, or the information gathering phase, testers collect as much information as possible about the target system. This phase is split into passive and active reconnaissance.
- Passive Reconnaissance – involves collecting information without directly interacting with the target systems. This might include gathering publicly available information, such as domain registration details or information shared on social media.
- Active Reconnaissance – involves direct interaction with the target system, such as sending packets to a network to elicit responses. This approach can reveal more detailed information but may be detected by the target’s security systems.
- Tools and Techniques for Gathering Information – Tools like WHOIS lookups, DNS queries (using tools like `dig` or `nslookup`), and the use of search engines are common in passive reconnaissance. For active reconnaissance, tools such as Nmap or Nessus can probe networks and systems for open ports and services.
Scanning
This involves identifying live hosts, open ports, and the services running on those ports. Scanning is a more in-depth exploration of those services to discover potential attack vectors.
- Network Scanning Tools and Methodologies – Tools such as Nmap, Masscan, or Zmap are used to scan networks to identify live hosts and open ports. These tools can also sometimes identify the operating system and services running on the target hosts.
- Identifying Live Hosts, Open Ports, and Services – The focus is on mapping the network to understand its structure, identifying which hosts are active, which ports are open on those hosts, and what services (e.g., web servers, mail servers) are running.
Vulnerability Assessment
This phase identifies known vulnerabilities in the network, systems, or applications being tested.
- Tools and Techniques for Vulnerability Scanning – Vulnerability scanners such as Nessus, OpenVAS, and Qualys are used to automate the detection of known vulnerabilities. These tools can scan for thousands of known issues in software, configurations, and patches.
- Analyzing Vulnerability Scan Results – The results of the analysis of false positives and actual vulnerabilities must be carefully analyzed. The identified vulnerabilities are then prioritized based on their severity, potential impact, and risk.
Source: Tarian
Exploitation
This phase aims to gain access or extract valuable data by leveraging identified vulnerabilities.
- Exploiting Vulnerabilities – Using tools like Metasploit, testers attempt to exploit known vulnerabilities. The goal might be to gain unauthorized access, escalate privileges, or execute arbitrary commands on the target system.
- Demonstrating Impact -Successful exploitation is documented with evidence to demonstrate the potential impact. This often involves capturing screenshots, obtaining system information, or exfiltrating dummy data.
Post-Exploitation
The post-exploitation phase of network penetration testing focuses on what can be done once a system has been compromised. The primary objectives during this phase are to determine the value of the machine compromised, maintain access for further exploitation if necessary, and extract as much valuable information as possible without being detected.
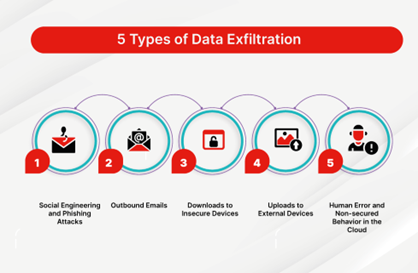
Access Maintenance and Data Exfiltration Techniques
- Access Maintenance – After gaining access, maintaining that access is crucial for further exploration and data extraction. This can be achieved by installing backdoors or Trojans, ensuring the attacker can re-enter the network easily. Tools like Netcat or custom scripts often listen on specific ports, allowing persistent access.
- Data Exfiltration Techniques -Once access is secured, sensitive data can be identified and extracted. Techniques vary from simple file transfers to more sophisticated methods like steganography, where data is hidden within other files or encrypted to avoid detection by network security mechanisms. Tools and scripts can automate the search for specific types of data, such as credit card information, personal data, or private information.
Source: Fortinet
Covering Tracks and Leaving No Trace
- Log Changes – Attackers often delete or alter logs that could reveal their activities to avoid detection. This includes logs from web servers, system events, and network devices.
- Use of Stealth Techniques – Techniques such as the use of rootkits or altering timestamps on files can help in concealing the breach. The goal is to make the intrusion appear as normal activity or, ideally, to leave no evidence that it ever occurred.
Reporting
The final phase of network penetration testing is reporting. This critical step involves compiling the test findings into a comprehensive report that outlines vulnerabilities, exploits, and recommendations to be fixed.
- Findings – The report should detail each vulnerability discovered during the test, including how it was found, its potential impact, and evidence of the exploitation (screenshots, logs, etc.). It should be technical enough for IT staff to understand and address the issues.
- Recommendation – For each finding, the report should offer clear, actionable recommendations for mitigation. These might include patching software, changing configurations, enhancing security policies, or conducting further staff training.
The post-exploitation and reporting phases are crucial for understanding network vulnerabilities’ real-world implications and guiding the process of fixing them. By carefully executing these phases, penetration testers can provide valuable insights that help organizations strengthen security measures and protect against future attacks.
TOOLS & TECHNOLOGIES
Network penetration testing uses various tools and technologies to find and exploit vulnerabilities and assess network security. This section covers popular tools, tips for choosing the right ones for different testing phases, and how to keep them updated and understand their legal implications.
Overview of Popular Tools
- Nmap (Network Mapper) – Nmap is a free and open-source tool for network discovery and security auditing. It is widely used for network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets to determine available hosts on the network, their services along with details, operating systems they are running, type of packet filters/firewalls in use, and other characteristics.
- Metasploit Framework -The Metasploit Project is a computer security project that provides information about security vulnerabilities and aids in penetration testing and IDS signature development. It’s a tool for developing and executing exploit code against a remote target machine. Metasploit can be used to test the vulnerability of computer systems or to break into remote systems.
- Wireshark – Wireshark is a network protocol analyzer that lets you see what’s happening on your network at a microscopic level. It is the de facto (often de jure) standard across many industries and educational institutions for deep network analysis.
Choosing the Right Tools
- Reconnaissance – Tools like Maltego can gather information about targets through open-source intelligence (OSINT) techniques. TheHarvester and Shodan are also useful for gathering email addresses, subdomains, and even open ports associated with the target.
- Scanning – Nmap is invaluable for scanning and helps identify open ports and services. Nessus and OpenVAS are widely used for vulnerability scanning, offering comprehensive databases of known vulnerabilities.
- Vulnerability Assessment – After identifying potential vulnerabilities, tools like QualysGuard or Nexpose can be used to conduct deeper vulnerability assessments and generate reports detailing the weaknesses found.
- Exploitation – The Metasploit Framework is key for this phase, allowing testers to exploit known vulnerabilities. Burp Suite is another essential tool for web application testing, providing various features to map out and exploit vulnerabilities.
- Post-Exploitation – Tools such as Mimikatz extract credentials and other sensitive information from compromised systems. Cobalt Strike offers post-exploitation capabilities, including maintaining access and lateral movement.

Keeping Tools Updated and Understanding Their Legal Implications
- Regular Updates – Security tools and technologies are constantly evolving to address new vulnerabilities and enhance functionality. Regularly updating these tools is critical to ensure the effectiveness of penetration tests.
- Legal Implications – The use of penetration testing tools can have legal implications, especially if done without proper approval. Having explicit permission from the network owner before conducting a test is essential. Additionally, testers should be aware of laws and regulations that apply to data protection and privacy in their jurisdiction.
Choosing the right tools for each penetration testing phase is essential for assessing and improving network security. Updating tools and considering legal aspects are important for responsible and effective testing.
ETHICAL & LEGAL CONSIDERATIONS
Ethical and legal considerations are paramount in network penetration testing to ensure that activities are conducted responsibly, professionally, and legally. Understanding and adhering to these considerations protects the penetration tester and upholds the cybersecurity field’s integrity and trustworthiness.
Importance of Ethics in Penetration Testing
Ethics play a crucial role in guiding the conduct of penetration testers. Given the sensitive nature of the work, which involves probing for vulnerabilities and potentially accessing confidential information, ethical principles ensure that testers:
- Respect Privacy – Testers must respect the privacy of the business’s data and users. Accessing, disclosing, or altering data without explicit permission is unethical.
- Maintain Privacy– Information discovered during a penetration test is often sensitive. Testers must keep this information confidential and share it only with authorized individuals.
- Provide Honest Reporting – Findings and reports should be honest and unbiased. Testers must accurately represent their findings, including the potential impact of discovered vulnerabilities, without downplaying risks.
- Avoid Conflicts of Interest – Testers should avoid situations where their interests could improperly influence their professional judgment or actions.
Legal Framework and Compliance Requirements
The legal framework surrounding penetration testing varies by country and can include criminal, civil, and regulatory laws. Compliance requirements may also dictate how penetration tests are conducted, especially in industries handling sensitive data, such as finance and healthcare. Key legal considerations include:
- Approval – Obtaining explicit, written permission from the rightful owner or responsible authority of the target system is mandatory before conducting any testing. This permission should detail the scope of the test, the methodologies approved, and any limitations or restrictions.
- Data Protection Laws -Testers must be aware of and comply with data protection laws (e.g., GDPR in Europe and CCPA in California) that govern the handling of personal data during their testing activities.
- Criminal Laws – Laws such as the Computer Fraud and Abuse Act (CFAA) in the United States prohibit unauthorized access to computers and networks. Testers must ensure that their activities do not violate such laws.
Obtaining Permission and Working Within Legal Boundaries
- Explicit Permission – Before beginning a penetration test, it is essential to have explicit, documented permission from the organization owning the target system. This documentation should outline the scope of the test, including which systems can be tested, testing methods approved, and any off-limits actions.
- Scope of Approval – The scope of the approval should be clearly defined and strictly adhered to. Testers must not deviate from the agreed-upon scope, as doing so can lead to legal repercussions and damage the trust between the tester and the client.
- Legal Advice – Given the complex legal landscape, obtaining legal advice or consulting with a legal professional experienced in cyber law can help testers navigate the legal implications of their work and ensure compliance with relevant laws and regulations.
Ethical and legal considerations form the backbone of responsible penetration testing. By adhering to ethical principles and operating within legal boundaries, penetration testers can conduct their work effectively while maintaining the trust of their clients and the broader community.
NETWORK PENETRATION TESTING BEST PRACTICES
Network penetration testing is a critical component of a business’s cybersecurity strategy. To ensure that these tests are effective and do not harm the organization or its stakeholders, best practices must be followed from the planning stage to the execution and reporting phases.
Planning and Preparation Best Practices
- Define Clear Objectives—Establish what the penetration test aims to achieve. Objectives can range from identifying vulnerabilities in specific systems to assessing the network’s overall security posture.
- Scope Agreement – Work closely with the client or stakeholders to agree on the scope of the test. This includes defining which systems, networks, and applications will be tested and identifying off-limits areas.
- Legal and Ethical Considerations – Ensure all testing activities are authorized in writing and comply with relevant legal and ethical guidelines. This protects both the tester and the organization.
- Risk Assessment – Conduct a risk assessment to identify potential impacts of the testing on the business’s operations. This will help in planning measures to mitigate any identified risks.
- Communication Plan – Establish a communication plan that outlines how findings will be reported and who within the organization should be notified of critical vulnerabilities as they are discovered.
Conducting Tests Without Disrupting Network Operations
- Use of Testing Environments – Where possible, use separate testing environments that mirror the live environment. This can prevent disruptions to the working network.
- Scheduling – Conduct tests during off-peak hours if they must be performed on live systems. This minimizes the impact on business operations.
- Load Monitoring – Monitor the load on network resources during testing to avoid overwhelming systems, which can lead to disruptions or downtime.
- Incremental Testing – Gradually increases the intensity of the testing. Start with less intrusive tests and proceed to more aggressive techniques only if the systems handle the load without issues.
Network Penetration Testing (Net Pen Test) Services
At Tanner Security Consultants, we provide thorough penetration testing services to assist organizations in proactively identifying and resolving vulnerabilities within their IT infrastructure. Our ethical hackers and security experts use advanced methodologies and state-of-the-art tools to replicate real-world attack scenarios, helping you to test your defenses and safeguard your key assets.
- Internal Network Penetration Test – Our internal network penetration tests simulate an attack from within your organization, identifying vulnerabilities that malicious insiders or compromised devices could exploit. This service helps you understand the security posture of your internal network and implement necessary controls to safeguard sensitive information.
- External Network Penetration Test – External network penetration tests focus on your business’s external-facing IT network, such as firewalls, VPNs, and servers. By simulating real-world attacks from outside the organization, we identify potential entry points and vulnerabilities that external attackers could exploit.
- Cloud Penetration Testing – Our cloud penetration testing services secure your cloud environments against threats. We specialize in various cloud platforms to identify vulnerabilities and enhance security.
- AWS Penetration Test: Ensures your AWS environment is robust and compliant with industry standards.
- Azure Penetration Test: Secures your Microsoft Azure environment by identifying and mitigating vulnerabilities.
- Microsoft 365 Security Reviews: Provides comprehensive security reviews of your Microsoft 365 environment, offering actionable recommendations to enhance your cloud security posture.
Types of Network Penetration Tests:
- Black Box Penetration Test: Simulates an attack by an uninformed outsider, providing a realistic assessment of your network defenses.
- Gray Box Penetration Test: This test combines partial knowledge of your network with efficient security assessments, balancing the benefits of black-and-white box testing.
- White Box Penetration Test: This test involves complete knowledge of your network to identify deep-rooted vulnerabilities and assess internal security controls.
- Authenticated Penetration Test: This test uses valid user credentials to assess security from the perspective of a logged-in user, identifying vulnerabilities from malicious insiders or attackers with stolen credentials.
- Red Team Penetration Test: This test simulates an attack by an outsider, providing a comprehensive evaluation of your security defenses and incident response capabilities.
Ensuring Data Protection and Privacy
- Data Handling Policies – Adhere to strict data handling policies to protect any sensitive information that may be accessed during the testing. This includes encryption of data in transit and at rest, as well as secure storage and eventual safe deletion of any data collected during the test.
- Privacy Compliance – Ensure the testing complies with all relevant privacy laws and regulations, such as GDPR or HIPAA. This includes obtaining any necessary consent before testing begins.
- Sensitive Data Avoidance – Avoid accessing or extracting sensitive data unless necessary for the test. Only random versions are used if sensitive data must be accessed.
- Security Measures Post-Test – Following the test, ensure that any changes made to the system are reverted and all access granted for testing is revoked. Conduct a thorough review to ensure the system is returned to its original state, or better, based on the test findings.
Following these best practices in network penetration testing helps organizations identify and mitigate vulnerabilities effectively while minimizing the risk of disrupting operations or compromising data privacy. Careful planning, execution, and follow-up are essential to the success of penetration testing efforts and the network’s overall security.
LEARNING AND CERTIFICATION OPPORTUNITIES
Pursuing a career in network penetration testing requires a combination of theoretical knowledge, practical skills, and recognized certifications. These elements demonstrate a professional’s ability to identify and exploit vulnerabilities within network systems. Below is an overview of the certification pathways, learning and skill development resources, and tips for building a career in network penetration testing.
Overview of Available Certifications
- Offensive Security Certified Professional (OSCP) – Offered by Offensive Security, the OSCP certification is highly respected in penetration testing. It focuses on hands-on offensive information security skills, including penetration testing, exploit development, and web application testing. The certification exam is a challenging 24-hour practical test.
- Certified Ethical Hacker (CEH) – Provided by the EC-Council, the CEH certification teaches how to think and act like a hacker (a legal one). It covers the latest commercial-grade hacking tools, techniques, and methodologies hackers and information security professionals use to hack a business lawfully.
- CompTIA PenTest+ – This certification from CompTIA is designed for cybersecurity professionals tasked with penetration testing and vulnerability management. It covers the management of vulnerabilities, not just their exploitation. The exam includes multiple-choice and performance-based questions.

Resources for Learning and Skill Development
- Online Courses and Tutorials – Platforms such as Cybrary, Udemy, Coursera, and Pluralsight offer a range of penetration testing courses, from beginner to advanced levels.
- Books – There are numerous books on the subject, including “The Web Application Hacker’s Handbook” for Web App Security, “Penetration Testing: A Hands-On Introduction to Hacking” by Georgia Weidman, and “Metasploit: The Penetration Tester’s Guide.
- Practice Labs – Websites like Hack The Box, OverTheWire, and VulnHub provide practical labs and challenges that simulate real-world scenarios for hands-on learning.
- Community and Conference – Engaging with the cybersecurity community through forums, social media groups, and attending conferences such as DEF CON, Black Hat, and local BSides events can provide valuable learning opportunities and networking.
FUTURE OF NETWORK PENETRATION TESTING
Network penetration testing is rapidly evolving due to advances in technology and changing cybersecurity threats. As businesses rely more on digital systems, strong network security, including penetration testing, is crucial. This section looks at future trends in network penetration testing, new technologies, and the growing role of artificial intelligence (AI) and machine learning (ML).
Emerging Trends and Technologies
- Automation and Integration – The future of penetration testing will increase reliance on automated tools and processes integrated into the broader security ecosystem. Automation can enhance efficiency, allowing for more frequent testing and immediate identification of vulnerabilities. Integrated security platforms will enable seamless workflows from vulnerability detection through the fixing phase.
- Cloud and IoT Security – As organizations continue to migrate to cloud-based solutions and integrate Internet of Things (IoT) devices into their networks, penetration testing must adapt to these environments. Testing methodologies addressing cloud infrastructure and IoT device vulnerabilities will become increasingly important.
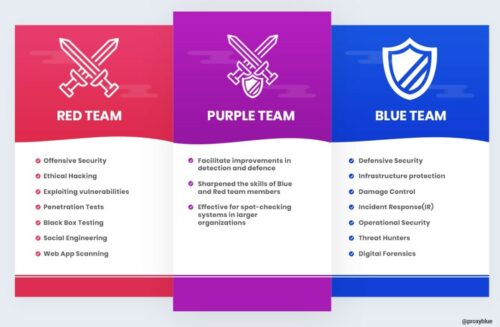
- Purple Teaming – This approach combines offensive (red team) and defensive (blue team) tactics, encouraging collaboration to enhance a business’s security posture. Purple teaming helps bridge the gap between detecting vulnerabilities and implementing effective defenses, promoting a more holistic view of security.
The Evolving Landscape of Network Security Threats
- Sophistication of Attacks – Cyber threats are becoming more sophisticated, with attackers using advanced techniques to bypass security measures. Penetration testers must stay ahead of these tactics by regularly updating their skills and knowledge.
- Rise of State-Sponsored Attacks – Cyber warfare and state-sponsored attacks are on the rise, targeting critical infrastructure and commercial entities. Penetration testing must consider these advanced persistent threats (APTs), requiring a deeper understanding of espionage tactics and countermeasures.
- Expanding Attack Surfaces – The expansion of remote work, cloud services, and IoT devices has broadened the attack surface of many organizations. Future penetration testing must address these extended boundaries, ensuring comprehensive coverage of all potential entry points.
The Role of AI and Machine Learning in Penetration Testing
- Automated Vulnerability Identification – AI and ML can analyze vast amounts of data to identify patterns and anomalies that may indicate vulnerabilities. These technologies can significantly reduce the time required to detect weaknesses in a network.
- Enhanced Attack Simulation –AI-driven tools can simulate sophisticated cyber-attacks, realistically assessing a business’s vulnerabilities. This can help develop more effective defense strategies.
- Adaptive Testing Techniques – AI and ML algorithms can adapt and learn from each penetration test conducted, improving their effectiveness over time. This continuous learning process can help predict future vulnerabilities and threats.
- Decision Support – AI can assist penetration testers in making informed decisions by ranking vulnerabilities based on their potential impact and the likelihood of exploitation. This helps allocate resources more effectively to address the most critical issues first.
The future of network penetration testing is influenced by new technology, changing cyber threats, and the use of AI and ML. As networks grow more complex and attacks become more advanced, penetration testing is crucial for protecting digital assets. Keeping up with these changes helps penetration testers offer essential protection against cybercrime.